 It’s amazing just how easy it is to crack passwords these days, Nate Anderson from ArsTechnica a self confessed script-kiddie shows in his article just how easy it was to crack 4,000 passwords in the space of a minute!
It’s amazing just how easy it is to crack passwords these days, Nate Anderson from ArsTechnica a self confessed script-kiddie shows in his article just how easy it was to crack 4,000 passwords in the space of a minute!
We all know how to build complex passwords:
- Include mixed cases, letters, number, symbols
- Change passwords regularly
- Avoid names especially of people you know
- And don’t repeat old passwords
All the things you would find in a good AD password policy
After ArsTechnica’s article there are probably a few more items you should add to that list next time you change your password.
The Long and Short
The experiment that Nate ran initially was focused on passwords of no more than 6 characters which he pretty much cracked in seconds regardless of adding symbols and mixed cases. But as the length of the passwords increased so to did the time. The chart below shows how a simple thing as increasing the length of a password from 6 characters to 9 dramatically increased the time taken to hack 17000 passwords using brute-force.
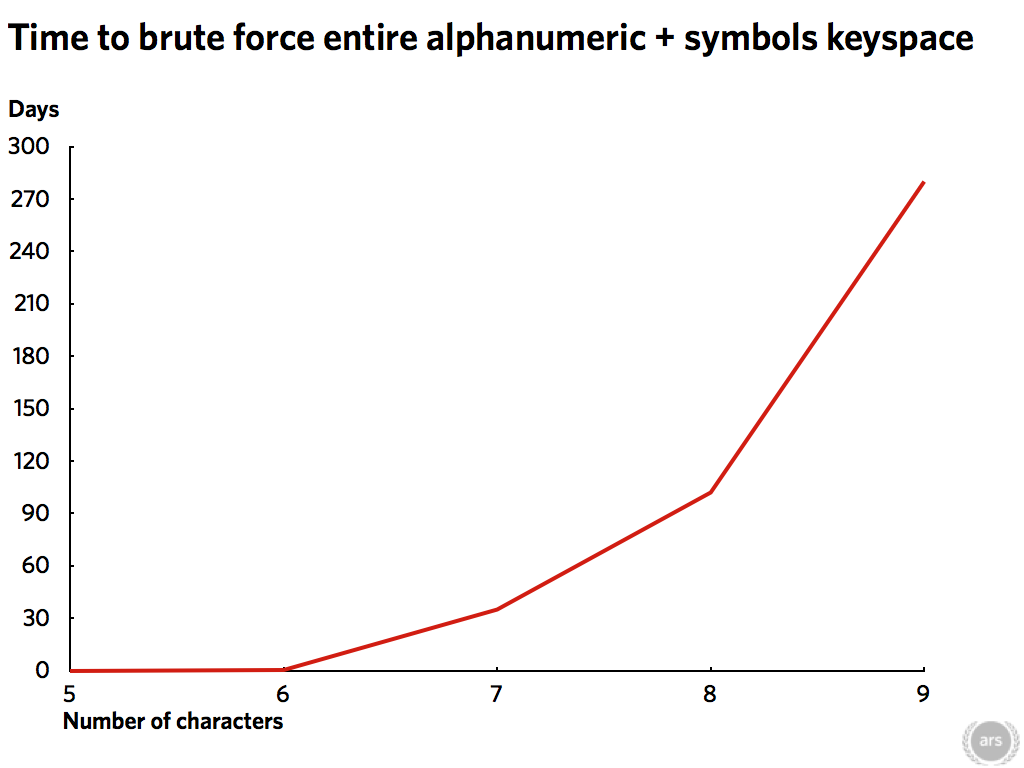
Avoid the pitfalls of small simple to remember passwords, long ones can be just as easy to remember.
Its all in the Patterns
One of the interesting points in the article is that hacking relies on patterns. Adding numbers and symbols you might think will help but if you stick to a common pattern for your passwords it really makes little difference. Avoid using typical password patterns like <word>+<3 numbers> or following the same one as your colleagues, once a hacker knows the pattern of one password they can pretty much expect all other accounts to follow the same rules.
Expanding Pool of Words
The number of words in the Oxford English dictionary exceeds well over 100,000 but the words used in most passwords is limited to a small subset of this the same set you’ll find in wordlists used by hacking tools. Avoid using common everyday words, consider words that are not common, everyday words.
Getting Everyone On-Board
Its all too common to find only some end users following password policies and it’s usually the ones that don’t who have the most to lose. If you’re having trouble convincing people then show them how quickly these guys were able to hack 16,000 passwords! Getting everyone’s buy-in on using more complex password policies improves your network security and your users all round.
Connect with us on LinkedIn, Spiceworks, Facebook, Twitter or Google+.
